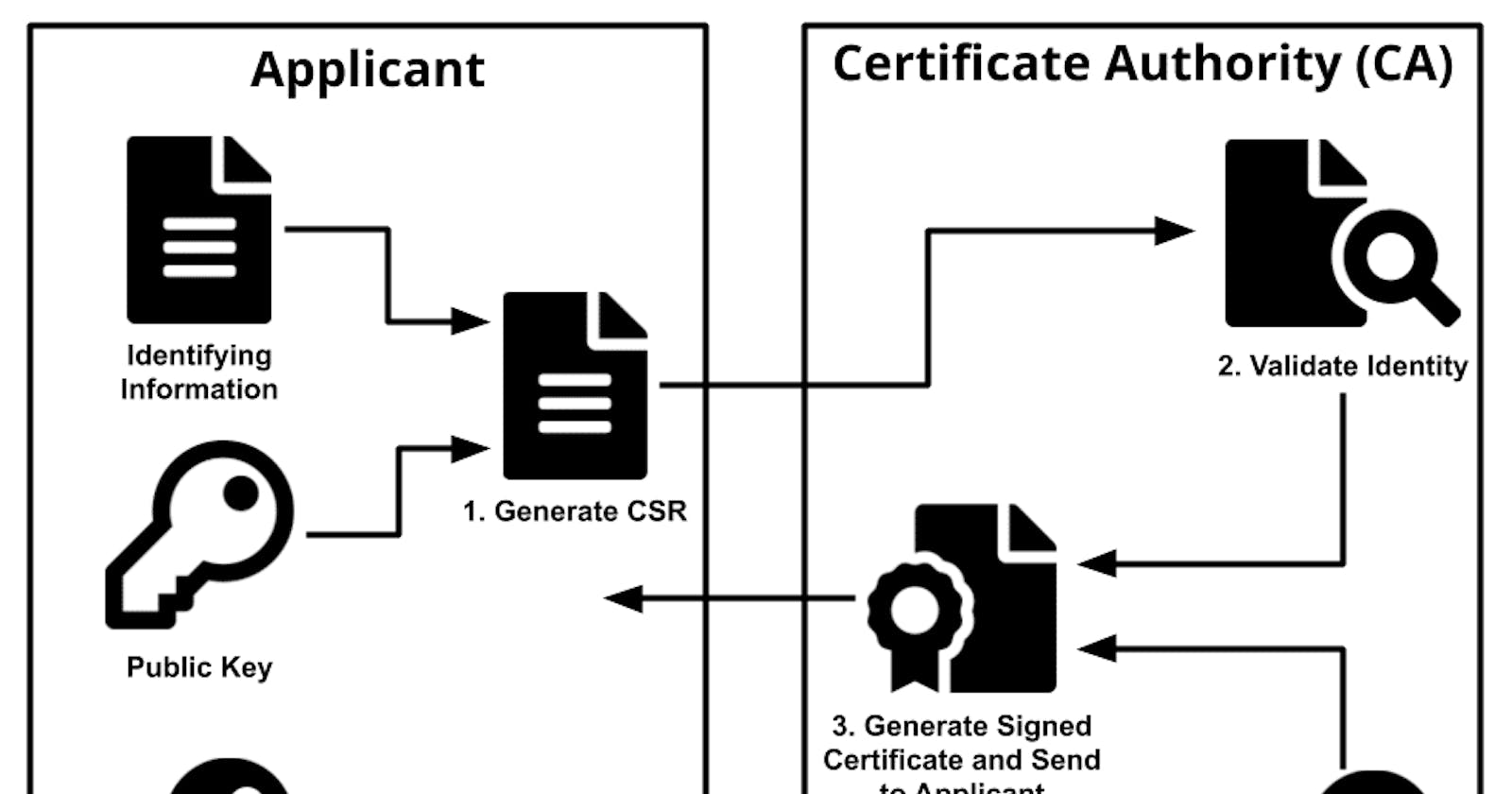
What's a CA anyway? Explaining the chain of trust that secures the Web
Are Certificate Authorities just a hoax to steal your money?
We live in the age of information: an absurd amount of data is transferred every day just through the web (which, by the way, is NOT the same thing as "the internet"), be it your shiny new Instagram story, your banking credentials, or what have you.
With so much information being handled, there needs to be some way to make sure it arrives to its destination unaltered and that only the intended recipient can read it: think about what would happen if just about anyone had all your passwords, that would be pretty bad right?
SSL to the rescue
But fear not! Some very smart people have in fact figured out a way to transmit information into the ether and have it arrive safely and away from prying eyes: SSL certificates, or better, the SSL protocol.
SSL stands for Secure Socket Layer, and it's what makes your browser show that nice green padlock next to the website's URL: a "guarantee" (in fact, a certificate) that makes sure your info is secure.
Technically, today we use TLS (or Transport Layer Security) as SSL was deprecated ages ago due to it being ridiculously insecure, but the name SSL certificate has stayed, and for all intents and purposes this terminology is fine

DigiCert is a popular Certificate Authority, or CA for short, which is an entity that signs and provides (in this case, selling them) trusted SSL certificates
Ensuring trust
So, you want to protect your website? It may sound like rocket science, but it's surprisingly simple, there's even a website that does all the dirty job for you (although I personally wouldn't trust it), but all of these alternatives have one characteristic: they're "self signed", which means they are not emitted by any registered entity like DigiCert or Let's Encrypt.
This may sound bad, but it's actually not an issue as far as security is concerned: SSL certificates (or more accurately your browser) will still encrypt all information that is sent and received to a website even if it is using a self-signed one. The issue arises when you want the browser to actually trust your certificate: you might have realized by reading that stackoverflow post I linked before, that the fatal flaw of self-signed certificates is that they cause browsers to whine about "Privacy Errors" or that "Your connection is not private" and to show a strikethrown red padlock instead of a green one as you'd expect, complaining that the website is not secure and that the owner may have malicious intents. There are ways to create your own trusted certificate authority and add it to your browsers, but it's a cumbersome process which will only work on your local machine, so it's not a viable option for production.
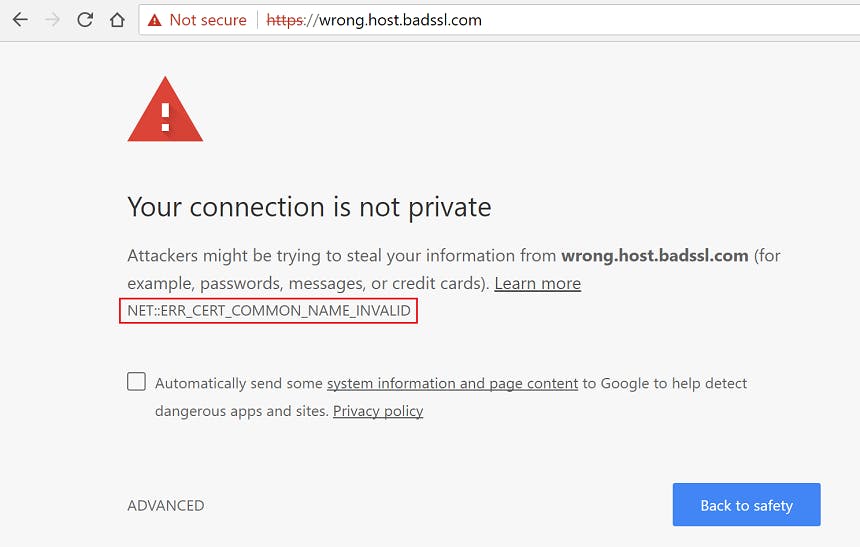
Google Chrome complaining about a self-signed certificate
Why CAs?
The idea behind a CA is that it makes it impossible for a third party to perform a MITM attack by pretending to be the site you're visiting and eavesdropping all of your traffic. If the browser had no way of knowing which certificate is the "right" one for a given website, a malicious user could just intercept your traffic, swap the website's certificate for his own so that he can see all of your traffic, and then forward it (encrypting with the website's certificate this time) to its intended destination so that you, the user, don't notice anything fishy going on: Boom, your precious credit card details are now in the hands of some Russian hacker, with all the implications that brings.
The problem of (most) CAs
Protecting user's traffic is a noble cause, but sadly (as with all things) companies have found a way to make this a business by selling trusted certificates for money, sometimes charging hundreds or even thousands of dollars for what's functionally identical to a self-signed certificate, except for the fact that the company's name is mentioned in your browser's list of trusted certificate issuers.
$600+ for a 3-year certificate from DigiCert, wtf?!
The light at the end of the tunnel
Fortunately for us though, there is hope: Let's Encrypt is a Certificate Authority that issues trusted SSL Certificates for free (they even have a super handy website to automate that). They last 90 days (but can be renewed free of charge indefinitely), not because they're free, but for security reasons (if a certificate lasts less time overall, there is a shorter time window during which it can be leaked!).
Yay, free SSL!
Conclusions
Whether your website needs an SSL certificate or not, knowing what options are out there might come in handy to you in the future: maybe you'll save a lot of money thanks to this article. Thank me later!